Deploying applications to development, staging and production never been so easy with GitHub Post-Receive Deployment Hook script!
Clone the script:
$ git clone https://github.com/kwangchin/GitHubHook.git
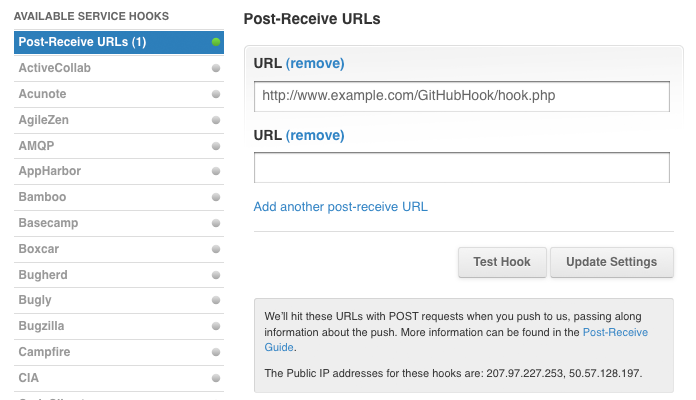
Go to your GitHub repo > Admin > Service Hooks, select Post-Receive URLS and enter your hook URL like this:
GitHub provides Post-Receive Hooks to allow HTTP callback with a HTTP Post. We then create a script for the callback to deploy the systems automatically.
You will need to create branches like stage and prod in Git before proceeding into the configurations.
You then can have a brief look into hook.php, a WebHook example provided for you to experience how simple the configurations are.
<?php
require_once('class.GitHubHook.php');
// Initiate the GitHub Deployment Hook
$hook = new GitHubHook;
// Enable the debug log, kindly make `log/hook.log` writable
$hook->enableDebug();
// Adding `stage` branch to deploy for `staging` to path `/var/www/testhook/stage`
$hook->addBranch('stage', 'staging', '/var/www/stage');
// Adding `prod` branch to deploy for `production` to path `/var/www/testhook/prod`
$hook->addBranch('prod', 'production', '/var/www/prod', array('[email protected]'));
// Deploy the commits
$hook->deploy();
In this example, we enabled the debug log for messages with timestamp. You can disable this by commenting or removing the line $hook->enableDebug()
We have a staging site and a production site in this example. You can add more branches easily with $hook->addBranch() method if you have more systems to deploy.
We then use $hook->deploy() to deploy the systems.
Worry about securities? We have enabled IP check to allow only GitHub hook addresses: 207.97.227.253, 50.57.128.197, 108.171.174.178 to deploy the systems. We also return a 404 Not Found page when there is illegal access to the hook script.
For better security, try hiding this hook script in deep directories like http://www.example.com/let/us/play/hide/and/seek/ and/or renaming the hook.php file into a40b6cf7a5.php.
We are trying to make developers life easier. Kindly fork this on GitHub and submit your pull requests to help us.