[NCR#1 Proposal] Z-Imburse: Proactive Reimbursement for Crypto-Native Organizations #5814
Pinned
jp4g
started this conversation in
[NRG#1] zkEmail
Replies: 1 comment
-
|
Congratulations on getting selected for NCR#1: https://github.com/orgs/noir-lang/discussions/5932 Check the announcement for what's next. Let's bring the world ZK! |
Beta Was this translation helpful? Give feedback.
0 replies
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment
-
Z-Imburse: Proactive Reimbursement for Crypto-Native Organizations
Summary
Work in the crypto ecosystem often presents situations where grantees pay for costs upfront, and some company or foundation eventually reimburses them for the funds. This slow, reactive, and bureaucratic process is an ironic antithesis of the infrastructure these organizations are building. We propose ZImburse: an Aztec-based web app for instant self-authorizing reimbursement dictated by organizational policies.
There are two classes of users in ZImburse:
We build this application from a perspective of a real problem we and many others face- just see DaoHaus's Cookie Jar extension. If ZImburse can achieve a reasonable UX, the likely adoption would lead to drastically reduced friction and overhead for organizations and contributors in web3 alike.
Methodology
In the MVP, there are three types of costs we can reimburse:
We can't include every service provider for each of these categories without having had generated a receipt through them, so our inclusion in the MVP will be limited to those we already have access to, including but not limited to the service providers listed above.
General Architecture of Reimbursement
We've mapped out an initial secure but unoptimized version of verifying a monthly hosting cost below:
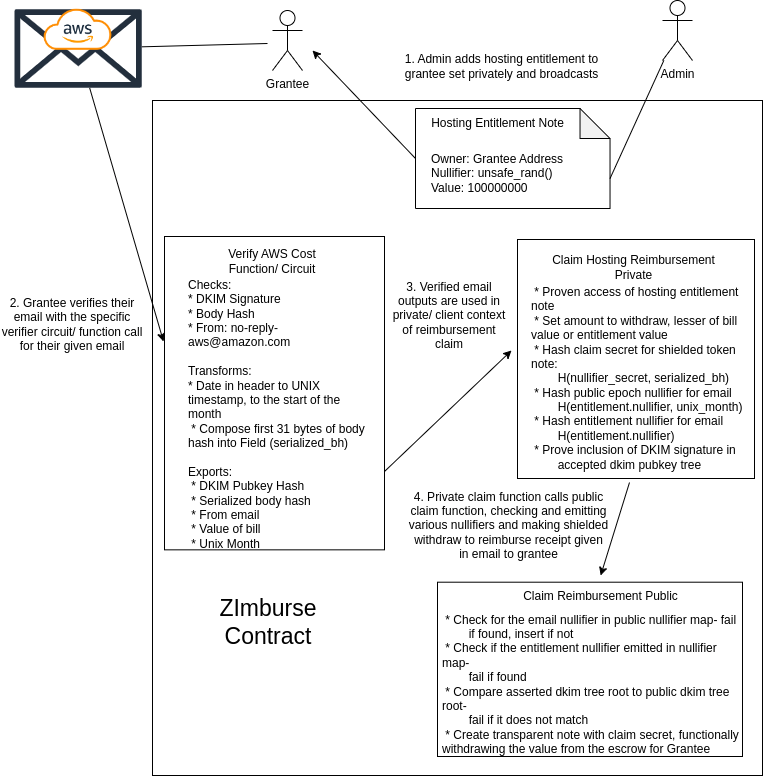
This is the general flow:
Admins should privately "enroll" grantees in the organization to allow them to claim organization-wide entitlements. This can be nullified by adding an additional nullifier check for users.
Admins will fund their ZImburse escrow contract with as much money as they think they will need. This should be done repeatedly as needed to top up grant funding.
Admins will create "Entitlement Notes" which are either made available publicly and immutably (for organization-wide entitlement) or added to a user's set of entitlement notes.
A grantee who is eligible for a given entitlement will use the corresponding email verifier function (circuit) to prove the authentic receipt of the email from an authorized service provider.
The verification exports all information needed to track the root of trust of the email, nullify against repeated use, evaluate whether the receipt applies for a given timeframe, and determine the value eligible for reimbursement.
A private call is used to prove access to entitlement notes (kernel), potentially to check timeframes, determine the reimbursement value, and generate any nullifiers and tree roots used publicly.
A public call is used to check the used DKIM pubkey, check for any existing nullifiers that prevent the user or email from being used, insert a new nullifier to "consume" the receipt in the contract, and finally release shielded tokens to the grantee according to the reimbursement policy.
The enumerated steps are for the specific case of hosting entitlements recurring monthly, however travel entitlements have a few extra steps around matching admin-defined locations and range-checking dates for receipts. We haven't mapped everything out down to exact specifics, and expect there are certain abstractions we will make that could afford a one-size-fits-all approach to entitlement notes and potentially even email verification.
ZKEmail.nr
Mach 34 has actually already built a functioning ZKEmail.nr library with the following capabilities in circuit:
Additionally, there is a rust command line that is used to perform the end-to-end transformation of
.emlfiles into a Prover.toml that performs these checks. Our code was derived by Olehmisar (Shield Swap) already, which has proven the efficacy of the pattern to drive logic in the Aztec sandbox.Outstanding components included or desired by traditional ZKEmail are described more below.
Partial Body Hashing
Noir exposes the "sha256_compression" black box function, meaning partial body hashing is readily available for integration. The majority of the work involved will be in the input generation library.
Quoted Printable Encoding
ZImburse will not immediately prioritize the inclusion of Quoted Printable Encoding- the NCR application specifically asks to focus on an end-user application. We can fully build an MVP proving that DAO's, companies, and foundations can use this infrastructure to facilitate proactive reimbursement policies without dedicated QPE decoder circuitry.
Work here can be prioritized over optimization and inclusion of as many additional sources of receipts as possible.
JS Library for Input Generation
ZKEmail.nr is written as a rust CLI. ZImburse as an Aztec dApp is a browser application interfacing with the official JS-based PXE, meaning we need to do the light work of reworking the rust CLI into a library with WASM bindings so that we can drive the input generation in a browser environment.
String Search vs Regex
There are many teams that have already proposed building regex in Noir and it is capitally inefficient for Aztec to fund R&D of two competing libraries when the success of one is already high.
We strongly posit that string searching is sufficient in the vast majority of cases, most importantly the header. Restricted to the header, there is no situation where, for instance, the string "to:" will appear anywhere other than as the recipient field in the header. In fact, this is likely the optimal path as regex will undoubtedly be more expensive. We additionally believe that string searching is sufficient (if a bit unweildy) for any query run over the body in our specific usecase.
As another team delivers their implementation of ZK-Regex, we would review the implementation and determine whether it makes sense to integrate into queries made over the body of the email.
Timeline
Forecasted dates are derived from a September 5th, 2024 reveal of the chosen proposals and are subject to be moved back in the unlikely event that finalists are not selected by then.
R&D (Week 1)
Sept. 6 to Sept. 12
Hosting Entitlements (Weeks 2-4)
Sept. 13 to Oct. 3
Report #1
Published October 3rd, 2024
Report on progress will detail the end-to-end integration of a web app driving contracts deployed to the Aztec sandbox
Travel Entitlements (Weeks 5-7)
Oct. 4 to Oct. 24
Wrap Up & Delivery (Week 8)
Oct. 25 to Oct. 31
Report #2
Published ~November 6th
We will take up to 1 week upon completion of the ZImburse MVP as we would like to create a writing that pitches the use of the application rather than just acting as a work report. This will likely include some video recordings, creating fake organizations people can easily join and test with fake USDC, etc.
Start Date
September 6th
Team Members
The Mach 34 team (Jack Gilcrest and Ian Brighton) will be responsible for delivering this work.
Aztec Ecosystem Work
EF PSE Work
Questions
What other receipts could we verify asides from hosting costs and travel receipts?
Can we inverse partial hashing to get the content at the start of an email?
How do we reconcile payments in alternative currencies? This oracle problem does not seem fun to solve in the private context; it would be much better if there were stablecoins on DEX's to use
Is it worth including ZK Passport to allow escrow managers to make commitments to names and grantees to prove ownership of matching commitments to add a layer of identity verification? Do we need them to also commit to nicknames that may appear if we want to check names on emails?
Can we abstract entitlement notes to "Spot" (one time use) and Monthly?
With PDF parsing, can we obtain more receipts? For instance, we wanted to include hotels but found most invoices were included as PDF attachments to emails.
Can we provide labels to addresses without using a server? Or does it make far more sense to have an end-to-end encrypted server to map names to addresses instead of relying on encrypted storage in Aztec (which will be public when iOS 99 ships with quantum computing) (should we add this to the deliverables because we probably need this)
Can we use the L1/L2 message bridge to extend functionality from a ZImburse instance deployed on Aztec to L1 Ethereum? Obviously on L2 the only reasonable option is to redeploy a version of this infrastructure with inferior privacy properties
Beta Was this translation helpful? Give feedback.
All reactions