- RSA (Rivest-Shamir-Adleman)
- AES (Advanced Encryption Standard)
- DES (Data Encryption Standard)
- OTP (One Time Password)
RSA is asymmetric key encryption algorithm which uses 2 key called public key and private key. Public key is used to encrypt the message while private key is used to decrypt the message. Mainly used for exchanging little information i.e digital signature.
- User has a generated key pair (public and private).
- Public key will be used to encrypt the data then it results cipher text. With the private key, cipher text will be decrypted.
- Each user can have more than 1 public key from different users, for they send the data (encrypt) to that user and the only way to read the sent message is by using receiver's private key.
src: https://medium.com/@jinkyulim96/algorithms-explained-rsa-encryption-9a37083aaa62
Signing asserts the authenticity of the data. RSA Signing often called "Signature" that is generated from the message using private key. User who wants to send the message have to send their signature as well signifies that the message actually came from the party by whom the public key is issued.
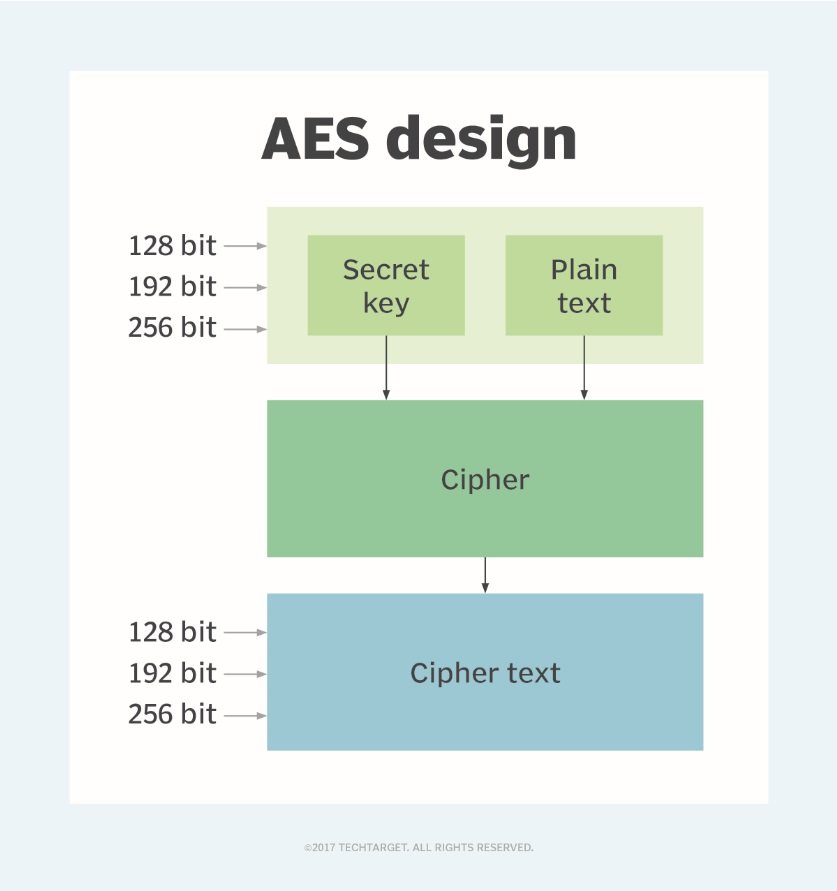
AES is a symmetric key encryption algorithm where one key can be used to encrypt and decrypt the message. AES is widely used for protecting data at REST and also for encrypted communications and secure data storage.
AES includes 3 block ciphers:
- AES-128 uses 128-bit key length to encrypt & decrypt a block of messages.
- AES-192 uses 192-bit key length to encrypt & decrypt a block of messages.
- AES-256 uses 256-bit key length to encrypt & decrypt a block of messages.
src: https://cdn.ttgtmedia.com/rms/onlineImages/security-aes_design.jpg
DES is a symmetric block cipher that encrypts data in blocks of size of 64 bits each (8 bytes), which means 64 bits of plain text go as the input to DES, which produces 64 bits of ciphertext. The same algorithm and key are used for encryption and decryption, with minor differences as figure shown below.
Meanwhile, 3DES or Triple-DES is a key-algorithm which applies DES algorithm 3 times to each data block.
src: https://media.geeksforgeeks.org/wp-content/uploads/20200306122641/DES-11.png
Google authenticator is a software-based authenticator implements 2 step verification services (commonly called as 2 Factor Authentication) to help identifying user's identity. This authenticator uses Time-based One Time Password (OTP) and HMAC-based OTP algorithm.
One of the advantages using 2FA over SMS-based verification is user don't need to worry about not getting the password/token/else because of their provider's issue or sim card gone. To solve the issue is to eliminate the dependency on the network provider.
TOTP (Time-based One Time Password) is an algorithm that computes OTP from a source of uniqueness (which I'm using here is a shared secret key), and current time.
HOTP (HMAC-based One Time Password) is an algorithm which uses hmac algorithm to generate OTP (n-digits deliver to user).