-
Notifications
You must be signed in to change notification settings - Fork 139
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
feature: Implement authentication for API v2 based on OAuth2 potocol. #388
base: master
Are you sure you want to change the base?
Conversation
| @@ -0,0 +1,85 @@ | |||
| from __future__ import annotations | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This import breaks FastApi's Depends. Related issue: fastapi/fastapi#1654
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
yeah i ran into this a long while ago at work, nice work actually tracking it down lol, that's not an easy error
app/api/v2/oauth.py
Outdated
| auth_credentials: Optional[dict[str, Union[str, int]]] = Depends( | ||
| auth_credentials: Optional[dict[str, Any]] = Depends( |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@alowave223 typing the possible values of a dict is usually a bad idea imo - if you're going to try, consider using a typing.TypedDict
|
there are also quite a few cases like this |
app/api/v2/common/oauth.py
Outdated
| # https://developer.zendesk.com/api-reference/sales-crm/authentication/requests/#client-authentication | ||
| def get_credentials_from_basic_auth( | ||
| request: Request, | ||
| ) -> Optional[dict[str, Union[str, int]]]: |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
better to use a TypedDict here, something like this so that the individual keys are statically typed
| # https://developer.zendesk.com/api-reference/sales-crm/authentication/requests/#client-authentication | |
| def get_credentials_from_basic_auth( | |
| request: Request, | |
| ) -> Optional[dict[str, Union[str, int]]]: | |
| from typing import TypedDict | |
| class BasicAuthCredentials(TypedDict): | |
| client_id: int | |
| client_secret: str | |
| # https://developer.zendesk.com/api-reference/sales-crm/authentication/requests/#client-authentication | |
| def get_credentials_from_basic_auth( | |
| request: Request, | |
| ) -> Optional[BasicAuthCredentials]: |
| @@ -0,0 +1,207 @@ | |||
| """ bancho.py's v2 apis for interacting with clans """ | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
some docstrings still out of date
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
left a review with some changes requested
overall i'd like to also reduce usage of typing.Union - better to constrain the variance of types when they come into our ecosystem so that we do not have to deal with this complexity ourselves
nice work so far! & sorry for the very late pr review lol
|
need to remember to bump version @ release |
|
started work, a couple of things stand out:
overall i think i'll continue to work on top of this pr, as it's quite decent at matching the spec so far -- nothing particularly wrong. |
It may also be worth storing other things, such as authorization grants and failed authorization attempts. |
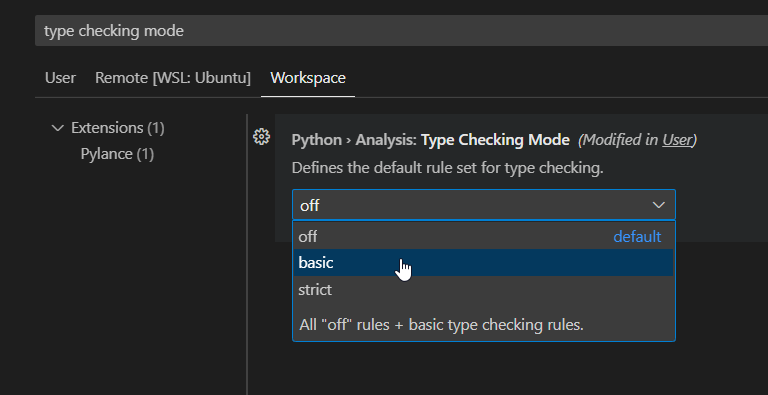
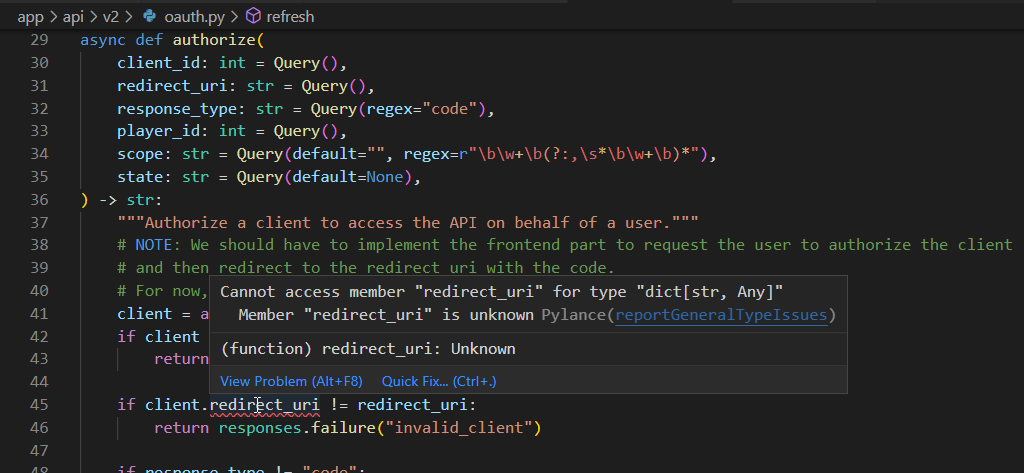
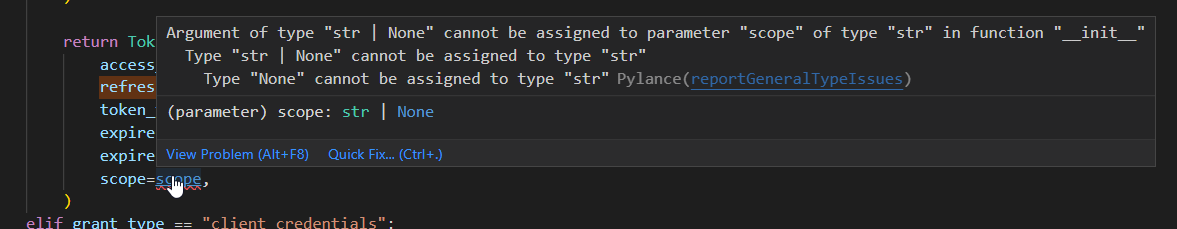
Describe your changes
Created authorization for third-party clients based on the OAuth2 protocol standard.
Related Issues / Projects
https://github.com/orgs/osuAkatsuki/projects/2
Checklist
make lint)