A threat actor is able to bypass the access controllers and gain access to the target
Clone this current repo recursively
git clone --recurse-submodules httbypassps://github.com/qeeqbox/authentication-Run the webapp using Python
python3 authentication-bypass/vulnerable-web-app/webapp.pyOpen the webapp in your browser 127.0.0.1:5142
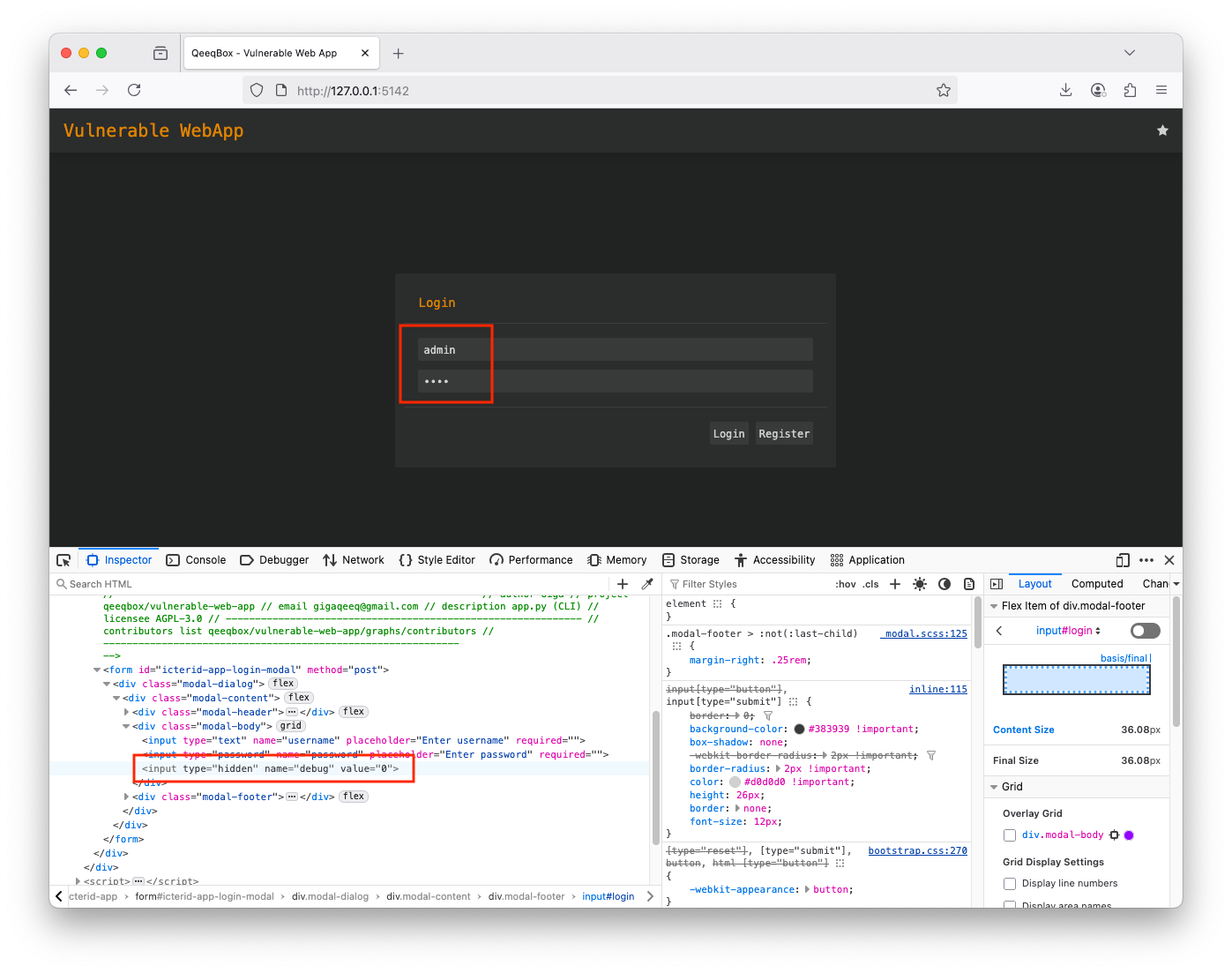
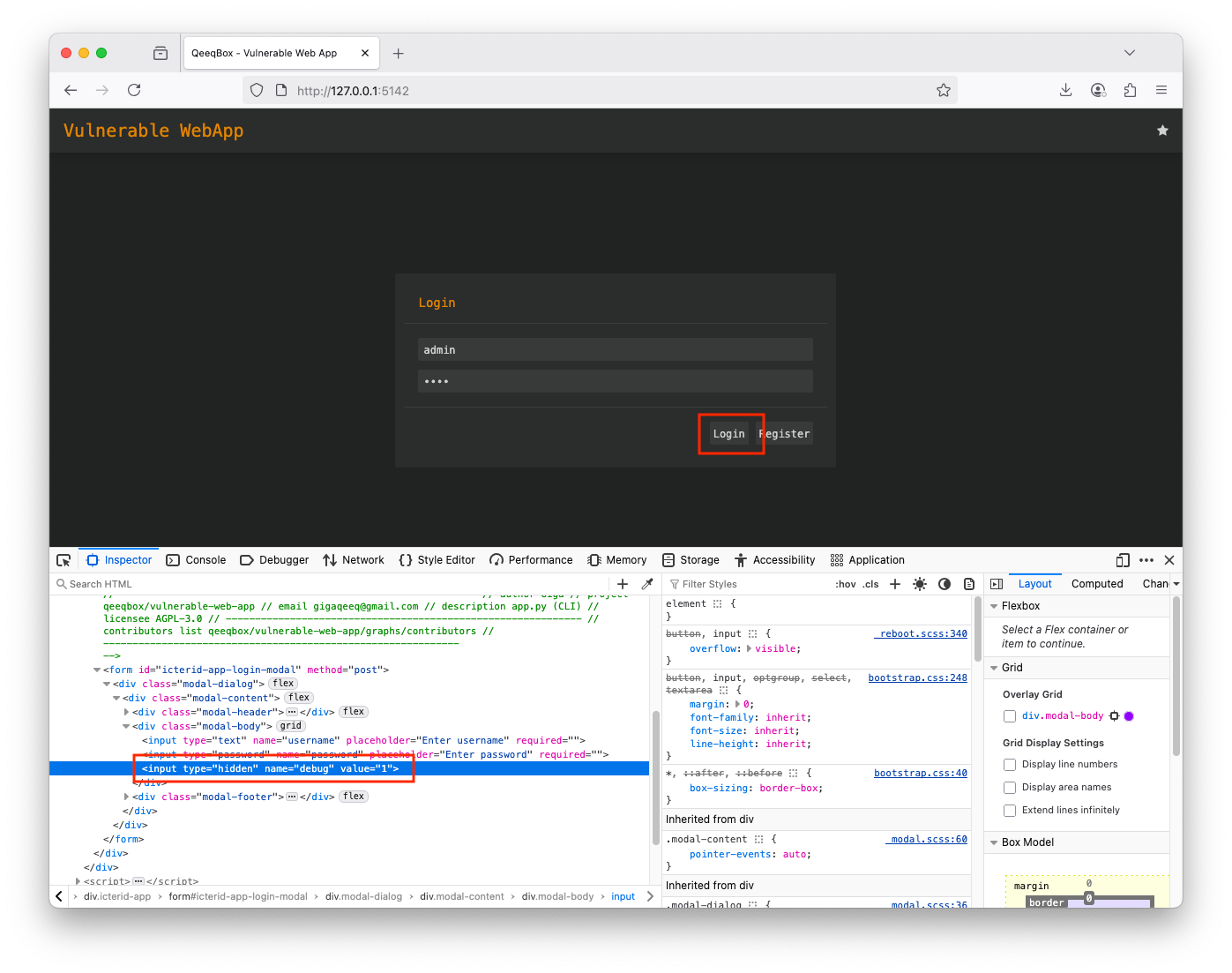
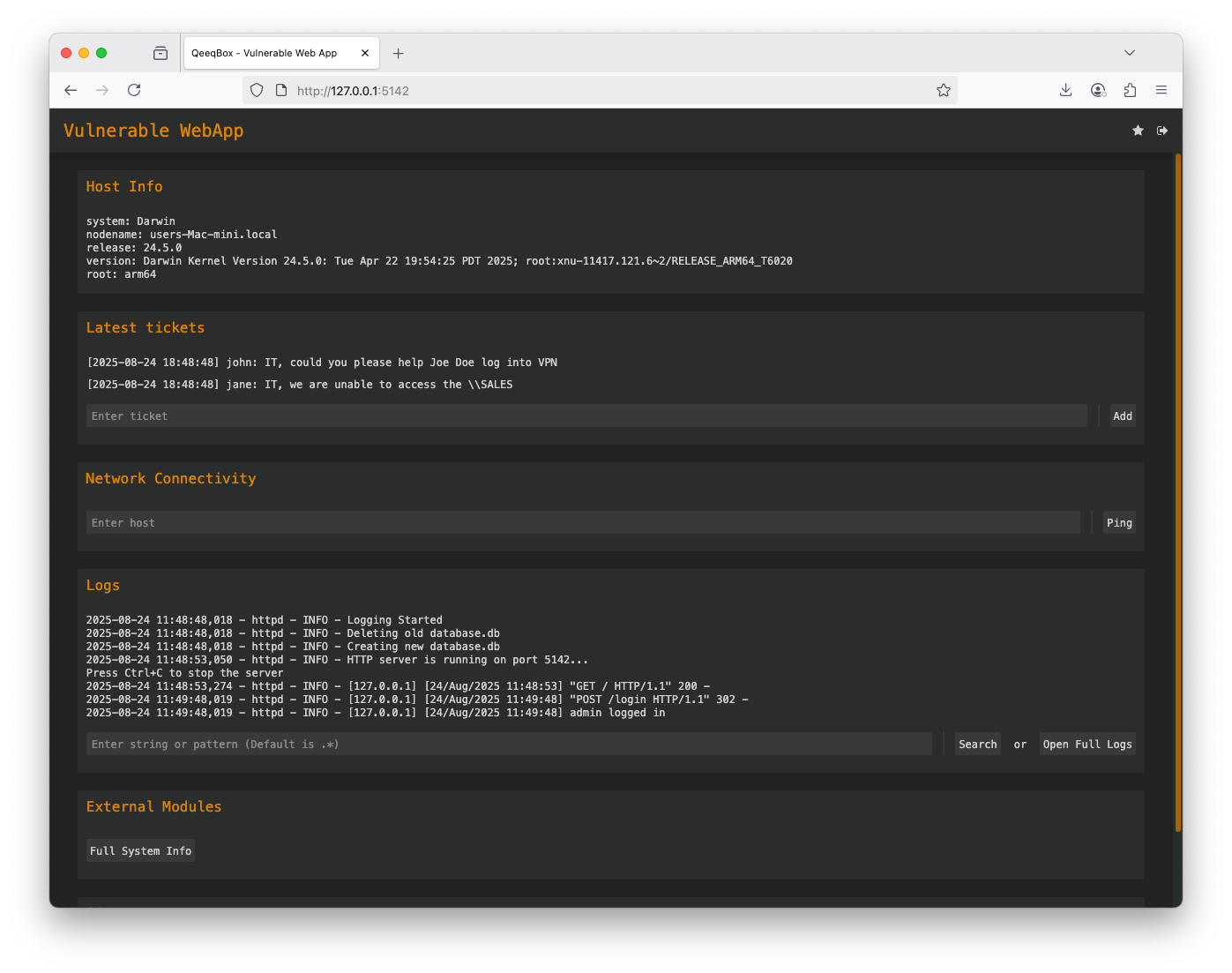
Right-click on the page and open Developer Tools, find the hidden variable named debug in the post form Change the variable debug from 0 to 1, this hit log in You are logged as adminWhen a user logs in using a username and password in POST request to the login route, a hidden variable called debug is checked, if it's 1, the
if parsed_url.path == "/login" and "username" in post_request_data and "password" in post_request_data:
ret = self.check_creds(post_request_data['username'][0],post_request_data['password'][0])
if isinstance(ret, list) and ret[0] == "valid":
self.send_content(302, self.gen_cookie(ret[1],60*15)+[('Location', URL)], None)
self.log_message("%s logged in" % post_request_data['username'][0])
return
elif isinstance(ret, list) and ret[0] == "password":
if "debug" in post_request_data:
if post_request_data["debug"][0] == "1":
self.send_content(302, self.gen_cookie(ret[1],60*15)+[('Location', URL)], None)
self.log_message("%s logged in" % post_request_data['username'][0])
return
self.send_content(401, [('Content-type', 'text/html')], self.msg_page(f"Password is wrong".encode("utf-8"), b"login"))
return
elif isinstance(ret, list) and ret[0] == "username" or isinstance(ret, list) and ret[0] == "error":
self.send_content(401, [('Content-type', 'text/html')], self.msg_page(f"User {post_request_data['username'][0]} doesn't exist".encode("utf-8"), b"login"))
return