Releases: radio24/TorBox
TorBox v.0.5.3 - 17.12.2023
Since October 2023, Raspberry Pi OS has been based on Debian 12 “Bookworm”. The only negative impact for TorBox was located in the installation script. The management of Python modules with pip3 was blocked. We fixed that issue and updated the TorBox image with the new Raspberry Pi OS. The new image works with Linux Kernel 6.1.21 and Tor version 0.4.8.10 with obfs4proxy version 0.0.14 and Snowflake 2.8.0.
Here are the links to the new updated TorBox v.0.5.3 (17.12.2023):
TorBox Image (about 1.25 GB): v.0.5.3 (17.12.2023) – SHA-256 values
TorBox Menu only: v.0.5.3 (17.12.2023) – SHA-256 values
Unfortunately, I have not yet been able to test the image with the new Raspberry Pi 5, yet.
TorBox v.0.5.3 - 09.07.2023
TorBox Image (about 1.1 GB): v.0.5.3 (09.07.2023) – SHA-256 values
TorBox Menu only: v.0.5.3 (09.07.2023) – SHA-256 values
Since we had to install additional software packages and update the configuration files, it is necessary to use the new image or reinstall TorBox using one of our installation scripts.
• • •
Changelog: v.0.5.2 –> v.0.5.3 (09.07.2023)
- Update: The system is based on Raspberry Pi OS “Bullseye” lite (64-bit) with Linux Kernel 6.1.21 and Tor version 0.4.7.13 with obfs4proxy version 0.0.14 and Snowflake 2.6.0. All installation scripts are updated to work with Raspberry Pi OS “Bullseye” (64-bit), Debian 11, 12, Ubuntu Server 22.04.02 LTS, and Ubuntu Server 23.04. We also improved the compatibility with Debian and Ubuntu and updated TorBox’s internal list of OBFS4 and Snowflake bridges.
- Update: Realtek RTL8821CU wireless network driver
- Update: TorBox Chat Secure version 2.0 (TCS). The idea behind the new version is to have a chatroom rather than only a person-to-person messenger. Also, by downloading a key, people can leave the chat room and log in later to see the “open” conversations and their messages in the private channels. All conversations are encrypted on the TorBox, but cannot be decrypted without the key. Turning TCS off will delete all encrypted data.
- New: The Danger Zone sub-menu collects features that are considered risky or could compromise the user’s security and anonymity. Therefore these features should only be used if the user knows the potential risks and consequences. For example, the “forwarding only” mode for client data traffic will function as a router without tor protection. This feature was also a request, but most of the time, it makes only sense in connection with developing and debugging.
- New: Also, in the Danger Zone sub-menu, we added the possibility of excluding domains from being routed through tor. TorBox will communicate directly with the destination without protection if the domain is on the exclusion list. For example, if you use TorBox in the country Authoritarian (.aaa), you may use tor for all communications, but not when you have to go to a governmental website (let’s say www.government.aaa). In this case, you can exclude government.aaa from being routed through tor. Another use case could be that you want to stream something that doesn’t need protection (for example, a local music station) but uses much bandwidth. Please remember that tor does not protect the traffic to/from the IPs on the exclusion list. It would be best to assume that everyone will see that you connect these IP addresses. If not correctly encrypted (for example, by using HTTP, which is blocked by default), everyone can see the content of the communication to/from these IP addresses!
- New: During the start-up of TorBox, by default, there is a failsafe in place to put TorBox’s AP back on wlan0 if it was used on wlan1. It will prevent a lock-out of the TorBox user. Based on another user request in the Danger Zone sub-menu TorBox’s AP can be permanently put on wlan1.
- New: In the configuration sub menu, we added support and generation of SSH keys for the TorBox login. If SSH public key authentication are configured, it is possible to turn off SSH password login in the Danger zone.
- New: WebSSH supports now SSH keys. Also, we applied the new style from TCS to WebSSH.
- New: In highly authoritarian countries connecting the tor network could be seen as suspicious. Because ISPs can see, log, and even block hostnames, the installation scripts and also the first start-up dialogue allow changing or randomizing the default hostname of the TorBox. There is also a new entry in the countermeasure sub-menu, which allows to change or randomize a hostname later. This feature was also based on user feedback.
- New: You can remove all tor bridges , fetch and use built-in bridges from the TorBrowser in the Update and Maintenance sub-menu. However, we think this is only a measure of last resort if nothing else gives you workable bridges.
- New: The Update and Maintenance sub-menu gives the possibility to synchronize TorBox’s time via ntp. If this fails, the user will be prompted to enter the right time and date.
- New: In the last TorBox version we added the possibility to exclude of slow relays. In this version we added the possibility to renew the exclusion list Update and Maintenance sub-menu.
- New: Insecure http requests are blocked by default. However, currently, there is no way to overcome the shortcomings of this kind of blocking. It will not work for applications and clients using TorBox’s SOCKS 5 functionality, in a VPN over Tor or a Tor over Tor situation.
- New: Using “AvoidDiskWrites 1” in torrc, which will lead to tor writing less frequently to disk than we would otherwise.
- Fixed: Snowflake and Meek functionality (they need local DNS resolution, which was still blocked).
- Fixed: The OFFLINE/ONLINE status of Snowflake- and Meek-Bridges is always labeled as OFFLINE in the bridge database. Therefore, the status is no longer taken into account and is removed.
- Fixed: VPN support.
- Fixed: Sometimes, pressing the ESC key didn’t close the menu, instead, it reloaded again.
- Fixed: The WLAN regulatory domain was not set permanently.
- Fixed: rc.local will now work more reliably and automatically establish a tor connection if possible and previously used.
- Improved: VPN over WLAN starts the Torbox Wireless Manager (TWM) if the connection with wlan0 is not established. It also supports captive portals deployed from WLAN. However, there is no need for captive portal support before connecting with the VPN provider (that was an error). Unfortunately, we couldn’t test all VPN-client/Internet interface combinations yet and need more feedback.
- Improved: If TorBox could not synchronize the system time during booting, tor would not load. The first start-up dialogue covers that, and if an automatic synchronization isn’t possible, the user will be asked for the correct date and time.
- Improved: Installing TorBox on unreliable bandwidth connections could be problematic. The install scripts have new added some tests to check if the necessary packages are installed. If packages are missing, the connection is rechecked and a new attempt to install the package is made. In some cases (for example go, tor, …), if the download of a package is not possible, the installation script try other ways to install it.
- Improved: Implementation of a new, more reliable way to install, update and check Python modules.
- Improved: The usability of reactivating Onion Services.
- Improved: TWM will work now with special characters. Also, is TWM confronted by WPS, it will not ask for a password.
- Improved: If the Bridge Relay is configured for the first time, but tor is not restarted, the user will be reminded to restart tor when looking up his personal OBFS4 bridge address.
- Improved: Res...
TorBox v.0.5.2 - 10.03.2023
With this update, we brought TorBox’s software to the latest state: Raspberry Pi OS “Bullseye” lite 64bit (Release date: February 21st, 2023) with the Linux Kernel 5.15.84 and Tor version 0.4.7.13 with obfs4proxy version 0.0.14 and Snowflake 2.5.1. We also fixed some critical bugs in connection with Snowflake and Meek, which blocked the correct functioning of these two bridges (see below). We added a better time synchronization to avoid problems with building tor circuits, especially in cases without Internet connectivity. As always, we appreciate feedback, ideas, bug reports, pull requests etc.
TorBox Image (about 1.1 GB): v.0.5.2 (10.03.2023) – SHA-256 values
TorBox Menu only: v.0.5.2 (10.03.2023) – SHA-256 values
Because this is an update, check the previous release for more details.
TorBox v.0.5.2 - 02.01.2023
Update – 16.02.2023
If TorBox is started for the first time, and the connection is selected through WiFi by the “first run” script, then synchronising the system clock certainly fails. As a consequence, tor will not be able to build a circuit. With this update, the “first run” script will newly display the system time and allow the user to synchronise the system clock automatically or manually. Also, we integrated a new menu entry in the Update and Maintenance submenu to synchronise the system clock.
• • •
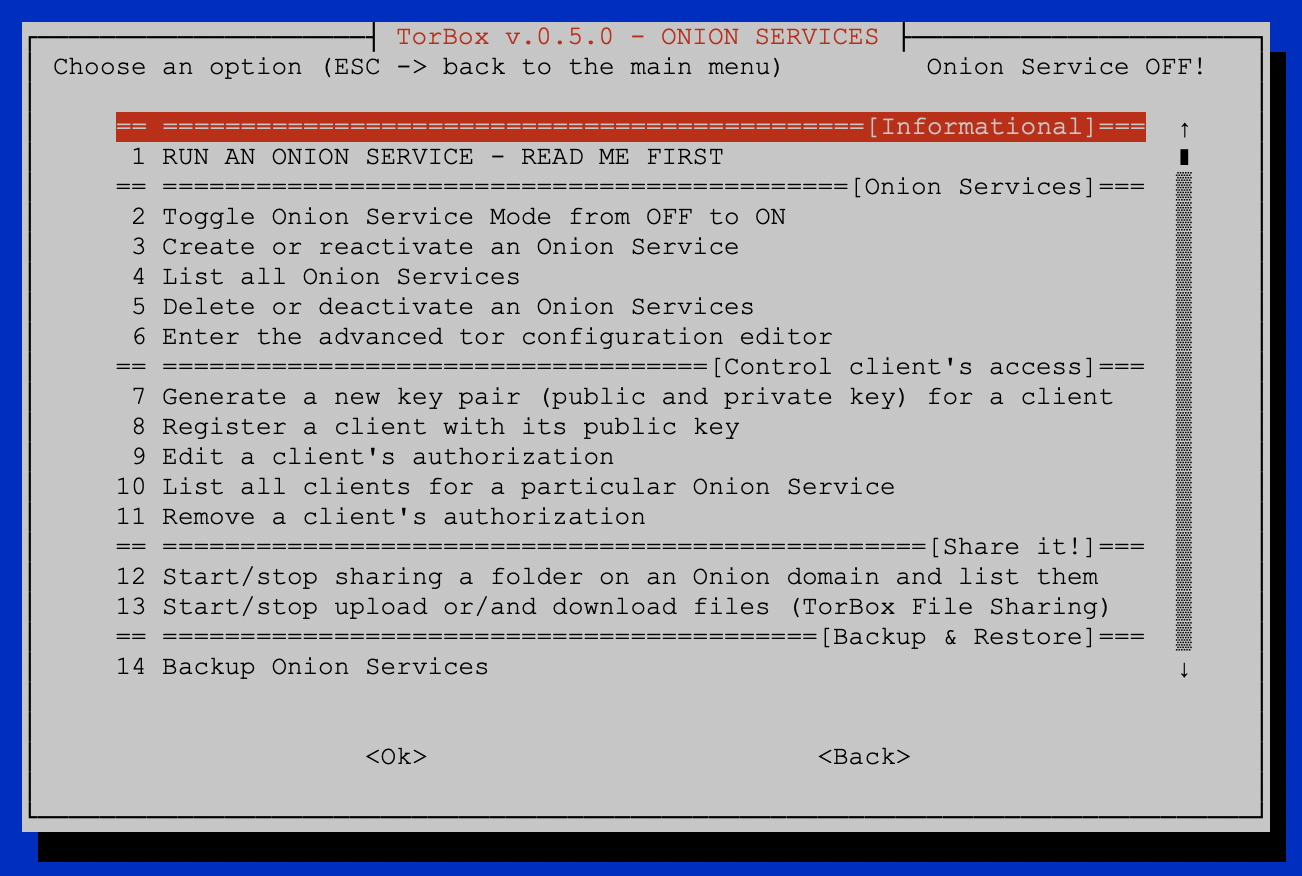
More than a year ago, we started to integrate Onion Services into TorBox. In the sub-menu Onion Services, it is easy to set up an Onion Service and to share a folder or a simple website, as well as TorBox File Sharing (TFS). With TorBox v.5.2, we additionally integrated TorBox Chat Secure (TCS). This is a secure way to communicate between two people using a specific onion domain. We still have some ideas for Onion Services for the following TorBox versions, for example, to allow users to install MariaDB/MySQL, PHP and WordPress through the menu so that dynamic website can be easily hosted on TorBox as an Onion service. Another idea currently under review is the further development of TCS into a chat room where several people can chat. With all these or other ideas, as well as eliminating errors and simplifying processes, active feedback from users is essential. Also, some bugs have been fixed in the new version, mainly as they occurred in our daily use. However, we still hear far too little from users. We appreciate feedback, ideas, bug reports, pull requests etc.
TorBox Image (about 1.1 GB): v.0.5.2 (02.01.2023) – SHA-256 values
TorBox Menu only: v.0.5.2 (02.01.2023) – SHA-256 values
Since we had to make substantial changes in the configuration files, it is recommended to use the new image or reinstall TorBox using one of our installation scripts.
• • •
Changelog: v.0.5.1 –> v.0.5.2 (02.01.2023)
- Update: The system is based on Raspberry Pi OS “Bullseye” lite (64-bit) with Linux Kernel 5.15.76 and Tor version 0.4.7.12 with obfs4proxy version 0.0.14 and Snowflake 2.4.1. Obfs4proxy version 0.0.14 will fix some critical obfuscation bugs. All installation scripts are updated to work with Raspberry Pi OS “Bullseye”, Debian 11 and Ubuntu Server 22.04 LTS. Additionally, we also updated TorBox’s internal list of OBFS4, Snowflake and Meek-Azure bridges.
- Update: Support for additional network drivers. We also moved the installation of additional network drivers from the installation to the “first use” script. Thus a kernel update during the installation will not break the installation of the drivers.
- Update: Noname 3.5″ TFT display support.
- New: ToBox Chat Secure (TCS) in the Onion Service sub-menu. TCS is a straightforward way to communicate between two people with safeguarding anonymity. No information about the conversation is stored on the TorBox.
- New: Support of handling multiple Snowflake bridge lines in the torrc. Similar to OBFS4 bridges, this feature will make circumventing tor blocking in countries like China, Iran, Russia and Turkmenistan more effective because you can select the right Snowflake bridge to activate according to the country in which you are located. Snowflake bridge lines can be activated, added, removed, deactivated and listed. However, currently, Snowflake supports only one active bridge line. If you activate several bridge lines, only the first will be used.
- New: Related to the point above, TorBox’s automatic fetching feature for OBFS4 and Snowflake bridges support now country-specific bridges. However, country-specific bridges are currently available only for certain countries (see also here). Also, if available, TorBox will fetch up to three bridges at once. To make these new features possible and to help people in censored countries, TorBox fetches bridges using the moat distributor. The moat distributor is an API that clients use to get bridges and circumvention settings. Clients must use domain fronting to avoid censorship when connecting to the API. In the case of TorBox, users in censoring countries have to use Snowflake or Meek-Azure to get more OBFS4 bridges (see here for more information).
- New: The “first-use” script is now supporting Snowflake, with the idea to make it easier for people in strictly censored countries to get TorBox running.
- New: Exclusion of slow relays (entry 15 in the Configuration sub-menu). Thanks to Nonie689 for bringing this idea up! Please test it extensively and give us feedback because we are considering adding this feature to the “first-use” script.
- New: Backup and restore cover the entire TorBox configuration (OBSF4 Bridge Relay, Onion Services and shared folders included). It can be found centrally in the Update and Maintenance sub-menu.
- New: Onion Services support client authorisation, which makes an Onion Service private and authenticated. With the former version, TorBox could control clients’ access from outside to TorBox’s Onion Services. With this version, we can provide the internal clients behind TorBox access to other Onion Services using the client authorisation on TorBox. In other words, if you register the server’s private key under the Onion Service menu entry 13, then not only the TorBox itself will have access to the Onion Service but also all client devices for which data traffic is routed through the TorBox, even if TorBox itself provides the Onion Service (in this case, TorBox is server and client). However, after the initial start, it can take up to 30′ minutes to take effect (thanks for figuring this out goes to nyxnor).
- Fixed: If Onion Services with shared folders were deleted, the removal of Nginx’s configuration failed.
- Fixed: Automatically adding bridges will work again. The script
bridges_get.pystarted to fail because the HTML generated byhttps://bridges.torproject.org/bridges?transport=obfs4%27has changed –> we added a patch written by lockcda (thanks for that!). Also, there is a bug in installing mechanise 0.4.8. For that reason, we still work with version 0.4.7. Anyhow, by using the moat distributor, this kind of problem should be gone. - Fixed: GitHub changed how it replies to the script’s question about the available tor versions. The changed behaviour broke the installation and update scripts, which are fixed now. We also removed the tor-specific entries in
torbox.runbecause of the complexity, and it doesn’t give an added value. - Fixed: Blocking HTTP plain text traffic doesn’t block access to webssh and .onion addresses anymore, which both work through HTTP. Please test it extensively and give us feedback because we are considering activating this feature as default in the next TorBox version.
- Fixed: Under certain circumstances, TACA, even if activated, couldn’t synchronize the clock.
- Fixed: Sometimes, pressing the ESC key didn’t close the menu, instead, it reloaded again.
- Fixed: The WPA password has to be between 8-63 characters – if the user changes this password, TorBox has to check it. Thanks to DEC-entralized finding that bug.
- Improved: To activate, remove and/or deactivate OBFS4 and Snowflake bridges, you no longer have to enter numbers of the concerning bridges, which you had to look up in the list. With this version, you can easily select the bridges you want to manipulate.
- Improved: OBFS4 and Snowflake bridges can be added and removed regardless of the actual type of connection. It gives the user, for example, the possibility to connect the tor network using Snowflake to automatically fetch country-specific OBFS4 bridges and then switch to OBFS4, which is more performant and more reliable than Snowflake.
- Improved: A new method of installing obfs4proxy ensures that the latest version is used. If the URL to the obfs4proxy repository is blocked, the version from the distribution will be installed, which could be outdated. Updating the base system in the Update and Maintenance submenu obfs4proxy will also be updated.
- Improved: The configuration reset using menu entry 6 in the Update and Maintenance submenu.
- Improved: The support for Ubuntu as the underlying operating system.
- Improved: Leaving the tor log with q instead of CTRL-C (improvement for the usability of webssh)
- Improved: If configured, the OBFS4 Bridge Relay will start directly after the boot. There is no need to log into the TorBox menu.
- Improved: The handling of the countermeasure against tightly configured firewal...
TorBox v.0.5.1 - 20.10.2022
Again, some time has passed since the initial release of TorBox v.0.5.1. Even if we already started to work on TorBox v.0.5.2, we decided to release an updated image of TorBox v.0.5.1 due to some critical fixes and a new tor version.
This version is based on Raspberry Pi OS “Bullseye” lite (64 bit) with Linux Kernel 5.15.61 and Tor version 0.4.7.10. It contains several major fixes to reduce memory pressure on relays and possible side-channel. It also includes a major bugfix related to congestion control to reduce memory pressure on relays. Finally, another major bugfix is related to Vanguard L2 layer node selection.
One bug in the initial release was that TorBox would not automatically add a bridge when that option was chosen in the Countermeasure sub-menu. This problem is in connection with mechanize 0.4.8. For that reason, we went back to version 0.4.7. Also, bridges_get.py failed because the HTML generated by https://bridges.torproject.org/bridges?transport=obfs4 has changed. To fix it, we added the patch from lockcda (see issue #173 on GitHub). Also, the way GitHub reports the available tor versions changed and broke the installation and update scripts. We fixed the affected scripts. Also, we removed the tor-specific entries in torbox.run because of the complexity, it doesn’t give an added value.
Here are the links to the new updated TorBox v.0.5.1:
TorBox Image (about 1 GB): v.0.5.1 (20.10.2022) – SHA-256 values
TorBox Menu only: v.0.5.1 (20.10.2022) – SHA-256 values
How to update an old TorBox v.0.5.1 (19.07.2022) installation?
You can perform the following tasks to update an older TorBox v.0.5.1 (19.07.2022) installation. This shouldn’t alter your custom-made configurations – however, I don’t promise anything (if needed, make a backup!).
- Please, make sure that TorBox has Internet connectivity.
- First, update the TorBox menu in the Update and Maintenance sub-menu (entry 5) to immediately benefit from the bugfixes.
- Press ESC until you have left the Torbox menu and find yourself back at the command line. Here use the following commands for
- removing mechanize 0.4.8:
sudo pip3 uninstall mechanize - installing mechanize 0.4.7:
sudo pip3 install mechanize==0.4.7
- removing mechanize 0.4.8:
TorBox v.0.5.1 - 19.07.2022
Honestly, TorBox v.0.5.0 was not one of our finest. When I started to fix some known problems and bugs almost a month ago, I found so much more. It was time to go into details and especially to fix to code added with version 0.5.0 – row by row. This version should run more reliable and stable than the versions before. Nevertheless, we also added and updated some of the features. However, once again, it shows also the importance of user feedback. Please report to us your problems and found bugs. We also need to know what you would like to see next and which features you request? With the TorBox GitHub repository, it is straightforward for everyone to report issues or change the code and propose it in a pull request.
TorBox Image (about 1 GB): v.0.5.1 (19.07.2022) – SHA-256 values
TorBox Menu only: v.0.5.1 (19.07.2022) – SHA-256 values
Since we had to install additional software packages and update the configuration files, it is necessary to use the new image or reinstall TorBox using one of our installation scripts.
• • •
Changelog: v.0.5.0 –> v.0.4.0 (19.07.2022)
- Update: The system is based on Raspberry Pi OS “Bullseye” lite (64 bit) with Linux Kernel 5.15.32 and Tor version 0.4.7.8. This version fixes several bug fixes, including a high severity security issue categorised as a Denial of Service. Everyone running an earlier version should upgrade to this version. Also, congestion control should improve traffic speed and stability on the network once most exit nodes upgrade. You can find more details about it in proposal 324 in the torspec.git repository. All installation scripts are updated to work with Raspberry Pi OS “Bullseye”, Debian 11 and Ubuntu Server 22.04 LTS. Additionally, we also updated TorBox’s internal list of OBFS4 bridges.
- Update: The installation script for Raspberry Pi OS had to be updated to work with the new Raspberry Pi OS images released in April. Also, starting with this version, TorBox will be only tested on the 64 bit version of the respective OS (Raspberry Pi OS, Debian and Ubuntu).
- Update:
vitorfrom nyxnor’s onionwash repository. - Update: the additional network driver so that they work with the new Linux kernel (unfortunately, Fars-Robotics didn’t update their network driver since October 2021).
- New:
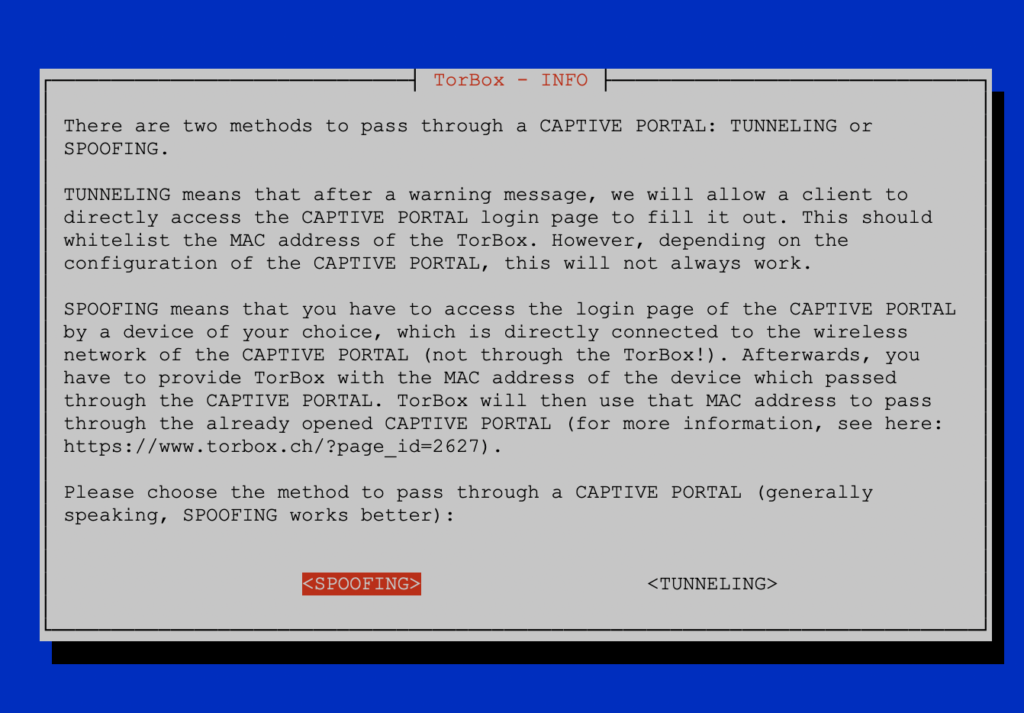
websshreplaces shellinabox, which seems it is not maintained anymore. Withwebssh, users don’t need a ssh client because every web browser can now jump in as a ssh client. A user on a wifi-client can type 192.168.42.1, someone on a cable-client 192.168.43.1. This functionality comes with a certain risk becausewebsshis not encrypted (this would need a self-signed certificate, which the browser doesn’t support easily). However, this shouldn’t cause any problems because the TorBox AP and its wlan or the connection cable should be controlled by you. By default,websshcannot be accessed from the Internet. If you seek maximum security, you still can keep using an ssh client and even deactivate thewebsshfunctionality in the Configuration sub-menu (entry 11). - New: There is a new way to pass through captive portals by SPOOFING the MAC address of a device that passed the captive portal successfully. Tests showed that some captive portals could be better overcome with the old method (TUNNELLING), some function better with SPOOFING and some need combined both ways. See here for more information.
- New: Starting with this version, TorBox randomises the MAC addresses on
wlan0,wlan1,eth0andeth1by default. You can change that behaviour and set your own MAC address in the Configuration sub-menu (entry 8). - Fixed: TorBox will not try to back up the OBFS4 Bridge Relay configuration if there is no such configuration.
- Fixed: It is impossible to simultaneously run the countermeasure against tightly configured firewalls and Snowflake, Meek and the OBFS4 Bridge Relay. This fix will prevent such a setting.
- Fixed: A bug broke the functionality on
ppp0andusb0. Also, before executingpon, TorBox will check ifpppdis already working and shut it down. - Fixed: Due to a little bug in the script, The menu entry, which should only activate OBFS4 bridges, which are ONLINE, fails to activate the OBFS4 mode properly. This bug prevents TorBox from deactivating the OBFS4 lines in the tor configuration file. Both are fixed.
- Fixed: Onion Service name bug (fixed by nyxnor).
- Improved: To prevent future bugs in the releases, a shellcheck Github action will be triggered with every pushed commit on the master repository.
- Improved: Local DNS resolution will be solely resolved through tor. This means that TorBox will not be able to resolve DNS requests from the local terminal if tor is not running. However, some functions, like Snowflake, Meek and time synchronisation, need clearnet DNS resolution to work without a running tor, but in this case, clearnet DNS resolution is explicitly activated for that purpose, and the user is asked or informed beforehand. DNS resolution from clients will always be made through tor, regardless of the settings. With the following commands in the terminal, local clearnet resolution can be set on/off (we will add that later in a “toxic “menu):
# Turn local clearnet DNS resolution on
sudo iptables -t nat -D OUTPUT -p udp --dport 53 -j DNAT --to 127.0.0.1:9053
sudo iptables -t nat -D OUTPUT -p tcp --dport 53 -j DNAT --to 127.0.0.1:9053
sudo systemctl restart dnsmasq
# Turn local clearnet DNS resolution off
sudo systemctl stop dnsmasq
sudo iptables -t nat -A OUTPUT -p udp --dport 53 -j DNAT --to 127.0.0.1:9053
sudo iptables -t nat -A OUTPUT -p tcp --dport 53 -j DNAT
- Improved: The use of Onion Services, sharing folder and TFS. For example, the sharing folder functionality and TFS can use every folder inside
/var/wwwregardless of the name of the Onion Service. This gives the possibility that an Onion domain namedx.onioncan share the folder/var/www/to_be_shared, and at the same time, TFS can control up- and/or downloads to/from the same folder using the Onion domainy.onion. - Improved: TFS can be started multiple times with different Onion domains. The file list is now alphabetically sorted. The message below the top banner can now display multiple lines (separated by a
\n). You can go into a sub-folder if you click on them, and if you start an upload in such a sub-folder, the uploaded files are placed there. Selecting multiple files and folders is now supported – they will be downloaded and compressed in a.zipfile to the local client. - Improved: Resetting Tor and enforcing a change of the permanent entry node in the update and maintenance sub-menu doesn’t deactivate the bridge and bridge relay mode anymore.
- Improved: Turning
systemd-journald.serviceoff by default to further reduce the logs.
TorBox v.0.5.0 - 03.07.2022
Six months have passed since the initial release of TorBox v.0.5.0. Version 0.5.1 will probably be released at the end of this year. Nevertheless, it was time to fix some bugs in version v.0.5.0 (especially concerning using OBFS4 bridges). If you re-install TorBox (using the image file or one of the installation scripts), in the case of Raspberry Pi OS, you will find the 64bit version with the Linux kernel 5.15.32 and Tor version 0.4.7.8.
Also new in the update: The MAC addresses of the network interfaces are now randomized. At the same time, a new way of overcoming captive portals is introduced, which is based on manipulating the MAC address of the Raspi network interface that is connected to the Internet (we have already reported on this in the blog here; however, details about the implementation and use can be found here).
Here are the links to the new updated TorBox v.0.5.0 version:
TorBox Image (~1 GB) : v.0.5.0 (03.07.2022) – SHA-256 values
TorBox Menu only: v.0.5.0 (03.07.2022) – SHA-256 values
How to update an old TorBox v.0.5.0 (02.01.2022) installation?
You can perform the following tasks to update an older TorBox v.0.5.0 (02.01.2022) installation. This shouldn’t alter your custom-made configurations – however, I don’t promise anything (if needed, make a backup!).
- Please, make sure that TorBox has Internet connectivity.
- First, update the TorBox menu in the Update and Maintenance sub-menu (entry 5) to immediately benefit from the bug fixes.
- Update the base system, the additional network drivers and the Tor version: Go to the Update and Maintenance sub-menu and use entries 1, 2 and 4.
- Press ESC until you have left the Torbox menu and find yourself back at the command line. Here use the following commands:
sudo apt-get -y install macchanger
cd; cd torbox; sudo cp etc/rc.local /etc
- Reboot TorBox.
• • •
We need your feedback!!
We hope this version pleases you. However, we are dependent on feedback. It is not just about fixing bugs and improving usability, but also about supporting additional interfaces and hardware in future releases:
What do you like?
What should be improved (why and how)?
What would you like to see next? Which features do you request?
With the TorBox GitHub repository, it is straightforward for everyone to report issues or change the code and propose it in a pull request. Because we continue to travel around, it sometimes needs more time to address the issues and proposals.
For future versions, it is essential that we know what you need and want to see from the Onion Services implementation. Please feel free to use the discussion forum to tell us your needs.
TorBox v.0.5.0 - 02.01.2022
TorBox v.0.5.0 is a major upgrade because starting with this version, it not only can be used to help clients to access the Internet safely and circumvent censorship, it also allows to bring your content in a safe and uncensored way to the Internet. Again, nyxnor, with his OnionJuggler project, was a key driver behind the Onion Services implementation into TorBox. With this version, TorBox introduces Onion Service support to share a simple website or/and files through Onion Services. However, this is only the start; in subsequent versions, we plan to support Onion Service access management on TorBox itself, and also a secure chat module is already programmed by Zotil but not yet implemented due to a lack of time. The support of Onion Services has much potential for developing TorBox further, but because our time is limited, it is essential that you give us feedback, what you need and want to see in the next version. Please feel free to use the discussion forum to tell us your needs.
TorBox Image (about 985 MB): v.0.5.0 (02.01.2022) – SHA-256 values
TorBox Menu only: v.0.5.0 (02.01.2022) – SHA-256 values
Since we had to install additional software packages and update the configuration files, it is necessary to use the new image or to reinstall TorBox using one of our installation scripts.
Besides the support of Onion Services, TorBox brings additional updates, improvements and fixes:
- Update: The system is based on Raspberry Pi OS “Bullseye” lite with Linux Kernel 5.10.63 and Tor version 0.4.6.9. This version fixes several bugs from earlier versions of Tor. One important fix is the removal of DNS timeout metric from the overload general signal. During our test, we had the feeling that Tor version 0.4.6.9 works more stable and reliable than the versions before. All installation scripts are updated to work with Raspberry Pi OS “Bullseye”, Debian 11 and Ubuntu Server 20.04.3 LTS / 21.10. Additionally, we also updated TorBox’s internal list of OBFS4 bridges.
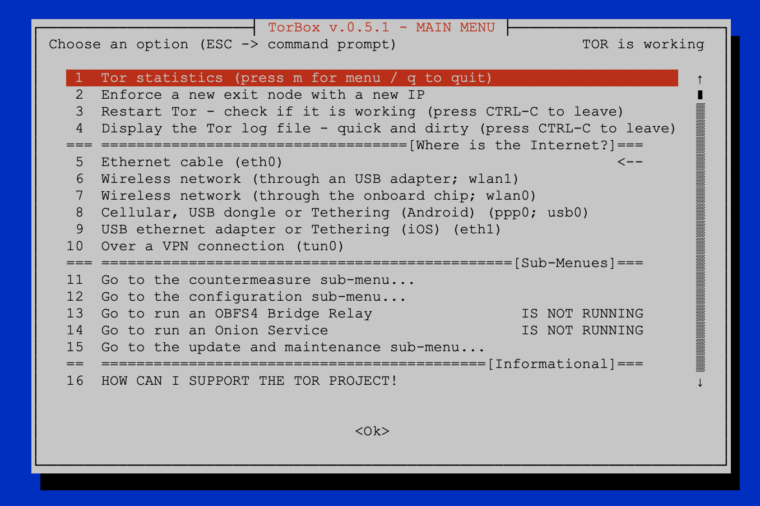
- New: The introduction of an Onion Services implementation allows the creation of Onion Services for public use or only for selected clients using client access restrictions. With the Onion Services sub-menu (see screenshot above; found in the “defend the open Internet” sub-menu), it is easy to share a folder with a static webpage, files etc. on an .onion domain with our without client access control, even if the TorBox is located behind a firewall, a network translator or placed in a censoring country. With TorBox File Sharing (TFS), upload and/or download files can be allowed to the public or specific clients.
- New: Since 2021, the TorBox team observed more and more providers (especially in connection with open hotspots) blocking ports needed for tor to work properly (tor commonly uses ports 80, 443, 9001 and 9030 for network traffic and directory information). Therefore, TorBox uses by default countermeasures against a tightly configured firewall taking care that tor uses only ports 80 and 443 for its data stream. We didn’t observe any negative impact (nevertheless, probably this feature should be deactivated if a bridge relay is run on the TorBox).
- New: torrc is now edited by nyxnor’s vitor, which checks the accuracy of tor configuration inside torrc before saving the new configuration file. This should avoid a broken tor configuration by using the advanced tor configuration editor. Vitor is part of the OnionJuggler project. Also, after changing tor’s configuration, TorBox is asking to restart tor.
- New: The team has been working hard to improve the code’s quality and introduced some basic coding guidelines, which we will implement step by step in the coming up versions. Also, we started to check the code with ShellCheck. Thanks to nyxnor for the inspiration!
- Improved: The “first-use” script introduced in TorBox’s last version had some major shortcomings, expecting the Internet is connected to the Ethernet interface. With TorBox v0.5.0, the “first-use” script was extensively rewritten. It supports now all the usual connection types. Additionally, if the countermeasures against a tightly configured firewall setting should stay activated, what we highly recommend.
- Improved: As part of our new basic coding guidelines, we rewrote the “Update and Reset” sub-menu, now called “Update and Maintenance”. At the same time, we improved the update routines, which also updates the installed Python modules and Snowflake (if tor is updated). The ability to remove all OBFS4 Bridge Relay Data was moved into the OBFS4 Bridge Relay sub-menu.
- Improved: The TorBox Wireless Manager (TWM) is now sorting the list of available wifi along with the signal strength. Hidden networks are only displayed after pushing the H key to declutter the main screen. Also, the code under the hut was again optimized (for example, a timeout was added if the AP doesn’t respond after sending a wrong password, optimizations for small screens and more).
- Improved: If TorBox’s WLAN is permanently disabled, the TWM tries to reconnect to a Wireless Network on
wlan0, not only onwlan1. However, ifwlan0andwlan1are available, TWM will prioritizewlan1(in this case, we think there is a reason why an USB wifi adapter is connected to the TorBox 😉). This also fixed an issue mentioned by connected201. - Improved: TorBox’s Automatic Counter Measures (TACA) checks after reconnecting with a wifi network if the interface got an IP address from the remote DHCP server. If this is not the case, it restarts the interface, triggering the request for a new IP. Also, TACA will detect if the system time is out of sync and re-synchronize it with ntpdate.
- Improved: Captive Portals are a pain in the ass! If the login page cannot be reached for whatever reason, TorBox provides a direct way back into the TWM (network reset included) to try it again. We have the experience that Captive Portals are getting harder to pass. However, currently, we are experimenting with another alternative way to deal with Captive Portals. If successful, we will add it immediately to TorBox v.0.5.0, which will be available after updating the TorBox menu in the “Update and Maintenance” sub-menu.
- Improved: Cable support is easier to accomplish now. We reviewed and simplified the code to achieve this goal. Consequently, we merged
set_interfaceandset_captiveintoset_interface_2andset_captive_2and removed the older files. This also fixed an issue mentioned by connected201. - Improved: Usability of the Countermeasure against a disconnection when idle feature.
- Improved: The tor log file is now shown with a filter to declutter the output, and “Bootstrapped 100% (done): Done” message is highlighted in white.
- Improved: The Bridge Relay backup file is placed into
~/backup. - Fixed: In the expert mode of the tor install scripts and the “Update and Maintenance” sub-menu, a hiccup due to a broken sort algorithm prevented the showing up of tor x.x.10 versions.
- Fixed: Even TorBox’s WLAN was permanently disabled, it was activated again when using
wlan0as an Internet source. This bug was reported by connected201. - Fixed: Snowflake is running again.
- Security: We must mask both tor services to ensure no use of tor connections before configuring TorBox with the “first use” routine.
- Security: Since the last TorBox version, all access to a tor related URL (for example,
torproject.org) directly from the TorBox have been done through tor for security reasons. Thanks to an advice from nyxnor, we switched to a more secure curl[SOCKS5](https://en.wikipedia.org/wiki/SOCKS)method (curl -x socks5h://127.0.0.1:9050). - Removed: Display of the Vanguards log because there is nothing interesting to see.
• • •
We need your feedback!!
We hope this version pleases you. However, we are dependent on feedback. It is not just about fixing bugs and improving usability, but also about supporting additional interfaces and hardware in future releases:...
TorBox v.0.4.2 - 02.08.2021
Again, thanks to several approaches by nyxnor, the core changes in TorBox v.0.4.2 is about hardening it (see also our discussion here). Our goal is to offer users in authoritarian countries the safest possible way to install and use TorBox. That said, I want to remind you once more that it is strongly advised not to use TorBox if your well-being depends on your anonymity. In such a situation, it is advisable to use Tails.
The hardening of TorBox also slightly changes the first time start procedure. After finishing the installation with the installation script or with flashing the image file of the SD Card (at least 8 Gb are necessary), login to the TorBox by using a SSH client (192.168.42.1 on a WiFi client and 192.168.43.1 on a cable client) or a web browser (https://192.168.42.1:9000 on a WiFi client and https://192.168.43.1:9000 on a cable client) is mandatory, because TorBox will ask the user during its first start to activate OBFS4 bridges for hiding the use of tor. The integrated OBFS4 bridges should help with that, although patience is necessary because that process could easily take 5 minutes to be successful. However, if you cannot connect to the Tor network yet, don’t panic – your selection is saved, and you can choose safely entry 5-10 in the main menu (we will improve the usability with the next version). This is only necessary during the first start after flashing the TorBox image on the SD cards. However, you can change your decision and configure the use of bridges later in the Countermeasure sub-menu.
TorBox Image (about 910 Mb): v.0.4.2 (02.08.2021) – SHA-256 values
TorBox Menu only: v.0.4.2 (02.08.2021) – SHA-256 values
Since we had to install additional software packages and update the configuration files, we recommend using the new image rather than updating an existing system. However, we have added a short guide at the end of this post for those who absolutely must update from the previous version (not older!).
Alternatively, you can download the latest Raspberry Pi OS Lite, ensure stable Internet connectivity, localize your installation with raspi-config (optional), download and execute our installation script (experimentally, we support also Debian and Ubuntu):
cd
wget https://raw.githubusercontent.com/radio24/TorBox/master/install/run_install.sh
chmod a+x run_install.sh
./run_install.sh
Changelog: v.0.4.1 (13.06.2021) –> v.0.4.2 (02.08.2021)
- Update: The system is based on Raspberry Pi OS “Buster” Lite with a Linux Kernel 5.10.52 and Tor version 0.4.6.6. Tor version 0.4.6.6 fixes several security issues, including a denial-of-service attack against onion service clients and another denial-of-service attack against relays. The 0.4.6.x series includes numerous features and bugfixes, including a significant improvement to our circuit timeout algorithm that should improve observed client performance and a way for relays to report when they are overloaded.
- Update: Internal list of OBFS4 bridges is actualized, and the Meek-Azure, as well as the Snowflake configurations are updated in
torrcbased on the Tor Browser 10.5.2. - Update: The Adafruit’s PiTFT display installer.
- New: The install scripts were extensively rewritten to be more reliable and secure in highly authoritarian countries. Tor will only be activated after a restart and a login by SSH or a web browser. This gives the user the possibility to start pluggable transports and bridges from the beginning to hide the use of tor in a better way and improve the user’s security. These improvements were proposed and highly influenced by nyxnor. Also, the installation script is more configurable, and these configurations will be stored into
run/torbox.runafter the installation. - New: Optional but highly recommended, automatic counter actions on log related events can be activated in the Countermeasure sub-menu. These counteractions should avoid the downtime of the connection to the tor network and give a better user experience, especially on connections with lower bandwidth. Most likely, this feature will be implemented as default in the next TorBox version. However, we are dependent on your feedback on this new feature. For more information, see under “Test and play with the ‘automatization’ feature“.
- New: Wifi driver for RTL8812b for Raspberry Pi OS added and for Debian/Ubuntu updated.
- Fixed: Access on the Tor Control port from the clients produces a warning message in the tor log. Even if we don’t assess this as a security risk, to avoid the warning message, access on the Tor Control Port from the clients is disabled by default but can be activated in the Configuration sub-menu.
- Improved: By default, all access to a tor related URL (torproject.org) will be done through tor for security reasons of users in highly authoritarian countries. This includes tor and Torbox menu updates as well as bridge fetching and checking. If a connection through tor is not possible, the user is asked if it is safe to access the URL directly. If the user agrees, the local DNS resolution will be made through public name servers to avoid cheap censorship mechanisms (for more information, see here); if the user disagrees, the access on the tor related URL is blocked.
- Improved: The file run/torbox.run is modified to a configuration file. The public name servers and the connectivity-check URL can be changed there and are used by every script (for more information, see here).
- Improved: Configuring the TorBox bridge relay allows to set the bridge distribution method (requested by DEC-entralized, see details in the commit d5b0045eec2e79c60dfd33b0239a5d1e4291597f).
- Improved: The configuration of the TorBox bridge relay can also be changed when the OBFS4 bridge relay is running. No deactivation before and activation after the changes are necessary anymore.
- Improved: Pressing ENTER in the TorBox bridge relay configuration dialogue doesn’t set the default values but the latest used ones.
- Improved: The installations scripts and the compatibility for Debian and Ubuntu systems as well as for 64 bit systems.
- Improved: We have a new way to set the hostname, which should avoid error messages.
- Removed: We don’t install tor from the Torproject repository anymore. As a fallback, a LTS version of tor is installed from the Raspberry Pi OS and the Debian repository (depending on your system), which is replaced from the latest stable version from the Tor’s Github Repository. This gives us a fallback – if someone uses the installation script and Tor’s Github Repository is blocked, the LTS version of tor is still installed, and the user can update to a newer version later through tor. So far, this is the best way to solve the „chicken or the egg“ problem.
- Removed: The
new_identscript is replaced by tor-prompt commands in the menu script (SIGNAL NEWNYM). - Experimental: Vanguards – Guard discovery and related traffic analysis protection – added (mentioned by nyxnor, see details in issue #72). Vanguards are optional and have to be activated in the Countermeasure sub-menu.
• • •
How to update from TorBox v.0.4.1 (13.06.2021)?
To update a TorBox v.0.4.1 (13.06.2021) installation, you can perform the following tasks. This deletes all your custom made configuration but not alter your bridge relay keys. Nevertheless, we recommend, if possible, using the new image.
- Please, make sure that TorBox has Internet connectivity.
- Update the system: Go to ...
TorBox v.0.4.1 - 13.06.2021
We are very dependent on your feedback! In this release, we have made an effort to implement more of your requests and, again, to improve the usability of TorBox based on your feedback. In this journey to the TorBox v.0.4.1, nyxnor has been a huge support, rewriting the OBFS4 bridge support of TorBox, which is now easier than ever to use. We also implemented experimentally “Shellinabox“, which gives clients to access the TorBox menu through a web browser so that the installation of a SSH client would not anymore be necessary. You can try it out by using https://192.168.42.1:9000 on a WiFi client and https://192.168.43.1:9000 on a cable client. Unfortunately, with the self-signed certificate for its secure connections, browsers will show a warning message during the first connection, which has to be ignored. We are eager to hear your feedback on “Shellinabox”. Do you know better alternatives? Let us know!
With the TorBox GitHub repository, it is straightforward for everyone to report issues or to change the code and to propose it in a pull request. Because we continue to travel around, it sometimes needs a little more time to address the issues and proposals. This is especially true for the TorBox website:
TorBox Image (about 940 Mb): v.0.4.1 (13.06.2021) – SHA-256 values
TorBox Menu only: v.0.4.1 (13.06.2021) – SHA-256 values
Since we had to install additional software packages and update the configuration files, we recommend using the new image rather than updating an existing system. However, we have added a short guide at the end of this post for those who absolutely must update from the previous version (not older!).
Alternatively, you can download the latest Raspberry Pi OS Lite, ensure stable Internet connectivity, localize your installation with raspi-config (optional), download and execute our installation script (experimentally, we support also Debian and Ubuntu):
cd
wget https://raw.githubusercontent.com/radio24/TorBox/master/install/run_install.sh
chmod a+x run_install.sh
./run_install.sh
Changelog: v.0.4.0 (10.04.2021) –> v.0.4.1 (13.06.2021)
- Update: The system is based on Raspberry Pi OS “Buster” Lite with a Linux Kernel 5.10.17 and Tor version 0.4.5.8.
- Update: Internal list of bridges updated.
- New: Installed with one of the installation scripts and using the option “–select-tor” makes it possible to chose the to be installed tor version.
- New: The installed tor version can be updated or changed with entry 5 in the Update and Reset sub-menu, where “DEFAULT” installs the latest stable version and “EXPERT” gives access to a variety of TorBox versions, including the -rc and -alpha versions.
- New: A new script was added to the torbox folder but not yet included in the TorBox menu, which should automatically react to log-related events. The idea behind it is that, with the next version, TorBox can automatically handle a disconnection from a WiFi network or the tor network. For example, if the tor log file indicates that the entry guard is failing, TorBox should choose a new entry guard in the background. If successfully tested, the necessary rules will follow later and are expected to be integrated into the Countermeasure sub-menu.
- Fixed: Using entry 10 in the Configuration sub-menu to enable the SSH access to TorBox from the Internet was not permanent when chosen so, but was permanent when chosen temporary (mentioned by bhafer, see details in issue #46).
- Fixed: SOCKS v5 port for destination address stream isolation was falsely set on port 9051 used for the Tor Control Port. The port is now changed to 9052.
- Fixed: The Tor Control Port (9051) is now accessible from clients (mentioned by bhafer, see details in issue #46).
- Fixed: OBFS4 bridges with IPv6 addresses are now handled correctly (see details in issue #55).
- Fixed: After the installation, the go source package wasn’t removed from the home directory.
*Fixed: All known problems and bugs listed in the Blog entry to TorBox v.0.4.0. - Improved: The use and handling of OBFS4 bridges are now more intuitive and in line with the use of the Meek-Azure and Snowflake bridges. There is no need anymore to activate OBFS4 bridge functionality in two steps. Also, the explanation about the functionality of bridges, pluggable transports and their use was completely rewritten. This amazing work was done by nyxnor – thank you very much!
- Improved: If one of the pluggable transports (OBFS4, MEEK, SNOWFLAKE) will be activated, another already running pluggable transport will be automatically deactivated.
- Improved: When installed from the image file, with the first start of the TorBox menu, the SSH server keys will be replaced by new ones. (mentioned by rsaxvc, see details in issue #40).
- Improved: All installation script can be run several times, for example, if the first installation attempt was not successful or when the system has to be reinstalled.
- Improved: The support for Ubuntu 20.04 / 21.04 and Debian 10/11 systems.
- Improved: Clean up the code of the TorBox Wireless Manager.
- Improved: We removed the first blank line to use the maximum available space for the entries in all menus. Also, the sub-menu to set up an OBFS4 relay server on the TorBox looks now more similar than the Countermeasure sub-menu.
- Improved: Restarting tor is now accessible from the Main menu.
- Improved: The slack space of the TorBox image is now overwritten by zeros (with the program zerorfree). This probably is why the compressed image of TorBox v.0.4.1 is almost 220 MB smaller than the image of TorBox v.0.4.0 (thanks goes to rsaxvc for the suggestion, see details in issue #39).
- Experimental: “Shellinabox” added to the TorBox and setup on port 9000. With “Shellinabox”, users can access the TorBox main menu through a web browser using https://192.168.42.1:9000 on a WiFi client and https://192.168.43.1:9000 on a cable client. Unfortunately, with the self-signed certificate for its secure connections, browsers will show a warning message during the first connection, which has to be ignored. To use a secure connection between the web browser and Shellinabox, the user must accept this certificate. We are eager to hear your feedback on “Shellinabox”. Do you know better alternatives? Let us know!
• • •
How to update from TorBox v.0.4.0 (10.04.2021)?
To update a TorBox v.0.4.0 (10.04.2021) installation, you can perform the following tasks. This deletes all your custom made configuration but not alter your bridge relay keys. Nevertheless, we recommend, if possible, using the new image.
- Please, make sure that TorBox has Internet connectivity.
- Update the system: Go to the Update and Reset sub-menu, update the base system, the TorBox menu (entry 1 and 5) and after that, update to the newest version of tor (entry 4).
- To ensure that all necessary packages are installed, execute the following commands (please, make sure that you copy the entire line!):
sudo apt-get -y install hostapd isc-dhcp-server obfs4proxy usbmuxd dnsmasq dnsutils tcpdump iftop vnstat links2 debian-goodies apt-transport-https dirmngr python3-pip python3-pil imagemagick tesseract-ocr ntpdate screen nyx git openvpn ppp tor-geoipdb...