Tailpipe is the lightweight, developer-friendly way to query logs.
Cloud logs, SQL insights. Collects logs from cloud, container and application sources. Query and analyze your data instantly with the power of SQL, right from your terminal.
Fast, local, and efficient. Runs locally, powered by DuckDB's in-memory analytics and Parquet's optimized storage.
An ecosystem of prebuilt intelligence. MITRE ATT&CK-aligned queries, prebuilt detections, benchmarks, and dashboards, all open source and community-driven.
Built to build with. Define detections as code, extend functionality with plugins and write custom SQL queries.
See the documentation for:
Plugins and query examples are on the Tailpipe Hub.
Prebuilt detection benchmarks are on the Powerpipe Hub.
Install Tailpipe from the downloads page:
# MacOS
brew install turbot/tap/tailpipe# Linux or Windows (WSL)
sudo /bin/sh -c "$(curl -fsSL https://tailpipe.io/install/tailpipe.sh)"Install a plugin from the Tailpipe Hub for your favorite service (e.g. AWS, Azure, GCP):
tailpipe plugin install awsConfigure your connection credentials, table partition and data source. Here is an AWS CloudTrail example:
vi ~/.tailpipe/config/aws.tpcconnection "aws" "logging_account" {
profile = "my-logging-account"
}
partition "aws_cloudtrail_log" "my_logs" {
source "aws_s3_bucket" {
connection = connection.aws.logging_account
bucket = "aws-cloudtrail-logs-bucket"
}
}Download, enrich, and save logs from your source (examples):
tailpipe collect aws_cloudtrail_logEnter interactive query mode:
tailpipe queryRun a query:
select
event_source,
event_name,
count(*) as event_count
from
aws_cloudtrail_log
where
not read_only
group by
event_source,
event_name
order by
event_count desc;+----------------------+-----------------------+-------------+
| event_source | event_name | event_count |
+----------------------+-----------------------+-------------+
| logs.amazonaws.com | CreateLogStream | 793845 |
| ecs.amazonaws.com | RunTask | 350836 |
| ecs.amazonaws.com | SubmitTaskStateChange | 190185 |
| s3.amazonaws.com | PutObject | 60842 |
| sns.amazonaws.com | TagResource | 25499 |
| lambda.amazonaws.com | TagResource | 20673 |
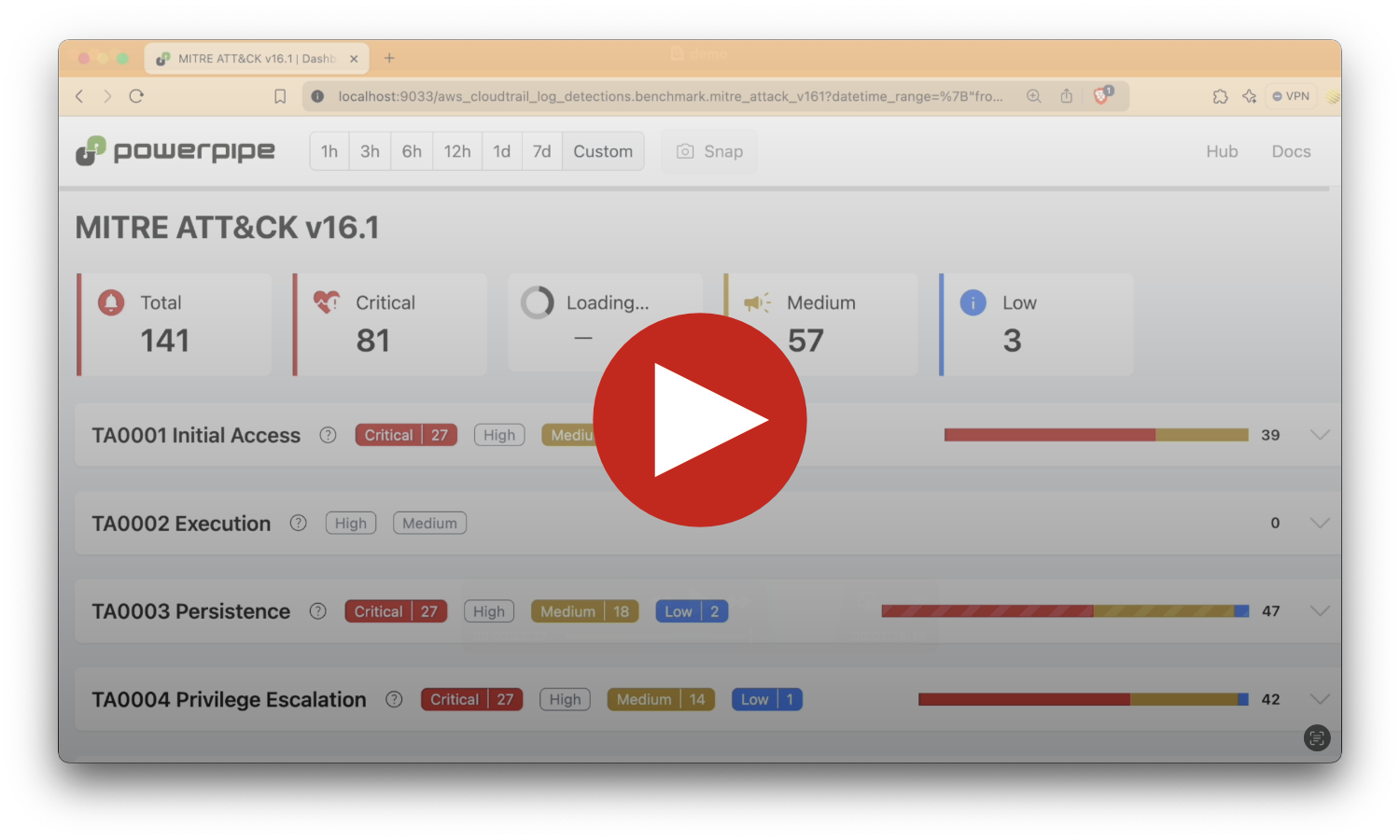
+----------------------+-----------------------+-------------+Pre-built dashboards and detections for the AWS plugin are available in Powerpipe mods, helping you monitor and analyze activity across your AWS accounts.
For example, the AWS CloudTrail Logs Detections mod scans your CloudTrail logs for anomalies, such as an S3 bucket being made public or a change in your VPC network infrastructure.
Dashboards and detections are open source, allowing easy customization and collaboration.
To get started, choose a mod from the Powerpipe Hub.
If you want to help develop the core Tailpipe binary, these are the steps to build it.
Clone:
git clone https://github.com/turbot/tailpipeBuild:
cd tailpipe
make
Check the version:
$ tailpipe --version
Tailpipe version 0.1.0
This repository is published under the AGPL 3.0 license. Please see our code of conduct. Contributors must sign our Contributor License Agreement as part of their first pull request. We look forward to collaborating with you!
Tailpipe is a product produced from this open source software, exclusively by Turbot HQ, Inc. It is distributed under our commercial terms. Others are allowed to make their own distribution of the software, but cannot use any of the Turbot trademarks, cloud services, etc. You can learn more in our Open Source FAQ.