-
Notifications
You must be signed in to change notification settings - Fork 48
en | Technical | KeePassRPC
In order to transfer passwords to and from KeePass, KeeFox needs to install a KeePass plugin called KeePassRPC. This plugin can communicate with other applications (not just KeeFox) provided that you allow it. This document explains the changes in KeePassRPC 1.3 (included with KeeFox 1.3) and links to more detailed technical documentation about the new version.
Provided that you are running a new enough version of Firefox and KeePass, the upgrade to KeeFox 1.3 or higher will be smooth and easy so most users won't need to worry about the information here but you might want to read about upgrading from KeeFox 1.2 or the more general information about different versions.
When first installing or upgrading to KeeFox 1.3 you will find two corresponding dialogs on your system asking for a one-time password to secure the new connection, one from Firefox and one from KeePass. Simply put the password from the KeePass dialog into the Firefox dialog, click OK and wait a few seconds while the password is verified.
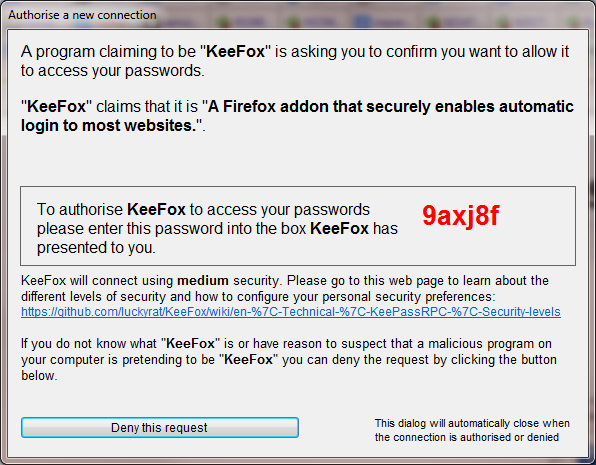
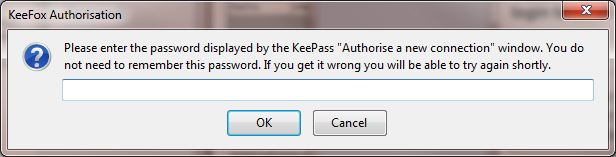
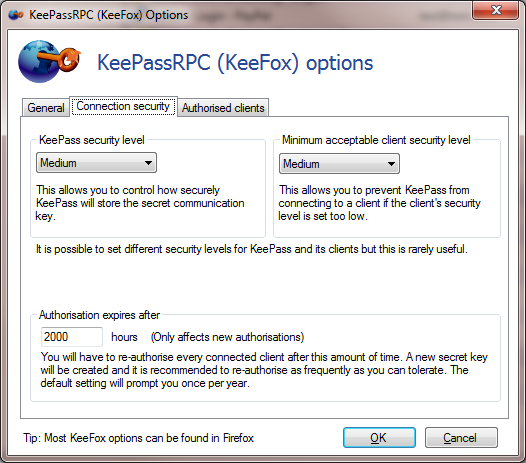
By default you will have to enter a new password once per year to protect against certain forms of attack but this setting is configurable in KeePassRPC options. The password authorisation dialog is there to protect you so do read the information displayed carefully, especially if the dialog appears unexpectedly.
The earlier KeePassRPC protocol is no less secure than it was when conceived 4 years ago but some aspects of the protocol design are less than ideal now that technology has improved.
-
Some parts of the protocol relied upon a hash algorithm that has been superseeded by a more secure algorithm. For the technical amongst you, I'm referring to SHA-1 vs SHA-2.
-
KeePassRPC requires a secure connection (just like the "HTTPS" connection your browser makes to secure websites). Every user of KeeFox needs a unique certificate (key) but web browsers like Firefox expect this certificate to be authorised by a trusted security organisation (which costs a lot of money) so KeeFox has to trick Firefox into accepting the certificate that KeePassRPC uses. It works, but it's not best practice and therefore always at risk of being broken by security policy changes in Firefox.
-
The secure connection requires the use of low-level network features that Firefox is alone in supporting (other browsers and Firefox mobile hide this feature from addons/extensions). Again, it works just fine at the moment but it is not the sensible way to implement a persistent network connection in 2013.
-
The certificate key used to encrypt the current connection is stored in the Microsoft .NET Key Store. Experience has shown that this is a rather fragile storage location
- it is too easy to accidentally connect to the wrong KeePass database (e.g. when multiple windows users are logged on at the same time)
- it is complex to repair when it goes wrong and there is no easy way for non-technical users to revoke access to unwanted secure connections.
- The new protocol brings the secret encryption keys under the control of KeePassRPC which will allow for far easier recovery from unforeseen problems.
KeePassRPC 1.3 and above will therefore use a new protocol that builds upon what we've learnt from the first protocol and takes advantage of new technology.
- Works over an insecure connection (no need for security certificates)
- Greater control over the level of security offered
- Existing client authorisations can be easily deleted
- Works with transports that are supported in all modern browsers and operating systems
When a KeePassRPC client (such as KeeFox) tries to connect to the KeePassRPC server it sends a variety of messages backwards and forwards between the client and server. These messages allow both the client and server to be certain that they are communicating with each other (rather than a malicious attacker) and a shared encryption key is created which the client and server can use to encrypt the contents of the messages being passed between them.
If it is the first time that the client and server have connected to each other, the user is asked to enter a server-generated password into the client.
The shared encryption key is normally stored for a reasonable length of time but when its expiry date is reached, a further password will be required.
Once the encryption key has been created, KeePassRPC uses it to protect the contents of messages that are sent using a format called JSON-RPC.
The earlier version of the KeePassRPC protocol also used JSON-RPC but it performed authentication after the establishment of a secure connection. Once the JSON-RPC part of the protocol is in use, the behaviour is very similar to the earlier version of the KeePassRPC protocol.
If anything goes wrong with the connection, you might find yourself being asked to enter a new password very frequently. This keeps your passwords secure but will no-doubt get annoying so please search the troubleshooting guide (post on the forum to start with because we have no trouble reports to shoot yet).
The information in this Wiki is out of date.
It is only of interest if you are using the old add-on called KeeFox in a very old (insecure) version of Firefox or other browsers based on the old Firefox XUL technology.
Read the manual for Kee and KeeBird instead.